Distance-Vector, Link-State and Path-Vector
Distance-Vector Routing Protocol
- A distance-vector routing protocol requires that a router inform its neighbors of topology change periodically.
- Routers running Distance-vector routing protocols knows only what his neighbors tells him. They do not have knoledge of the entire path to a destination. Instead they use two methods:
• Distance from its destination.
- Distance-vector routing protocols have less computational complexity and message overhead.
(The EIGRP routers exchange messages that contain information about bandwidth, delay, load, reliability and MTU of the path to each destination as known by the advertising router. Each router uses these parameters to compute the resulting distance to a destination. No further topological information is present in the messages. This principle fully corresponds to the operation of distance-vector protocols. Therefore, EIGRP is in essence a distance-vector protocol.
It is true that EIGRP uses a number of techniques not present in native distance-vector protocols, notably
•the use of explicit hello packets to discover and maintain adjacencies between routers;
•the use of a reliable protocol to transport routing updates;
•the use of a feasibility condition to select a loop-free path)
Link-State Routing Protocol
- Link-state routing protocol require a router to inform all the nodes in a network of topology change.
- Routers running Link-state routing protocol knows about the full topology of the network. They have knowledge of the entire path to a destination.
- Link-state routing protocols have high computational complexity and message overhead.
Protocols: OSPF, IS-IS
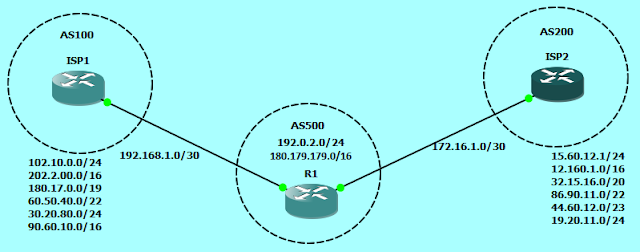
Path-Vector Routing Protocol
A path-vector routing protocol is a computer network routing protocol which maintains the path information that gets updated dynamically. Updates which have looped through the network and returned to the same node are easily detected and discarded.
Protocols: BGP



Hi, your blog is very informative & knowlegeful.
ReplyDelete